From Cybersecurity to Physical Procedures: Strengthening Company Protection in an Altering Globe
By incorporating the strengths of both cybersecurity and physical protection, firms can produce an extensive defense method that addresses the varied variety of risks they deal with. In this conversation, we will certainly discover the altering risk landscape, the need to incorporate cybersecurity and physical protection, the execution of multi-factor authentication steps, the significance of staff member understanding and training, and the adjustment of safety and security steps for remote labor forces. By checking out these vital areas, we will acquire beneficial understandings into exactly how companies can enhance their corporate security in an ever-changing globe.
Understanding the Transforming Risk Landscape
The progressing nature of the contemporary globe requires a comprehensive understanding of the transforming danger landscape for efficient business security. In today's interconnected and digital age, dangers to corporate safety and security have come to be much more complex and sophisticated. As technology advances and organizations end up being significantly reliant on digital facilities, the potential for cyberattacks, information violations, and other protection violations has significantly boosted. It is vital for organizations to stay informed and adjust their security gauges to address these developing dangers.
One key element of recognizing the changing risk landscape is acknowledging the different types of hazards that organizations encounter. Furthermore, physical risks such as burglary, vandalism, and corporate espionage continue to be prevalent concerns for services.
Tracking and analyzing the threat landscape is crucial in order to determine prospective risks and vulnerabilities. This involves remaining updated on the newest cybersecurity fads, analyzing hazard knowledge records, and performing regular threat assessments. By recognizing the altering hazard landscape, companies can proactively carry out appropriate security actions to reduce threats and shield their assets, online reputation, and stakeholders.
Integrating Cybersecurity and Physical Safety And Security
Incorporating cybersecurity and physical safety and security is essential for extensive business protection in today's interconnected and electronic landscape. As organizations progressively count on technology and interconnected systems, the borders between physical and cyber risks are ending up being blurred. To properly safeguard versus these risks, an all natural approach that combines both cybersecurity and physical security steps is essential.
Cybersecurity concentrates on shielding electronic possessions, such as networks, information, and systems, from unauthorized access, interruption, and burglary. Physical safety and security, on the various other hand, includes measures to secure physical properties, individuals, and centers from dangers and vulnerabilities. By integrating these 2 domain names, companies can deal with susceptabilities and hazards from both physical and electronic angles, thus improving their overall safety and security position.
The assimilation of these two disciplines enables a much more comprehensive understanding of safety threats and makes it possible for a unified reaction to occurrences. Physical access controls can be improved by incorporating them with cybersecurity procedures, such as two-factor verification or biometric recognition. Cybersecurity procedures can be complemented by physical safety and security steps, such as monitoring cams, alarm systems, and protected accessibility factors.
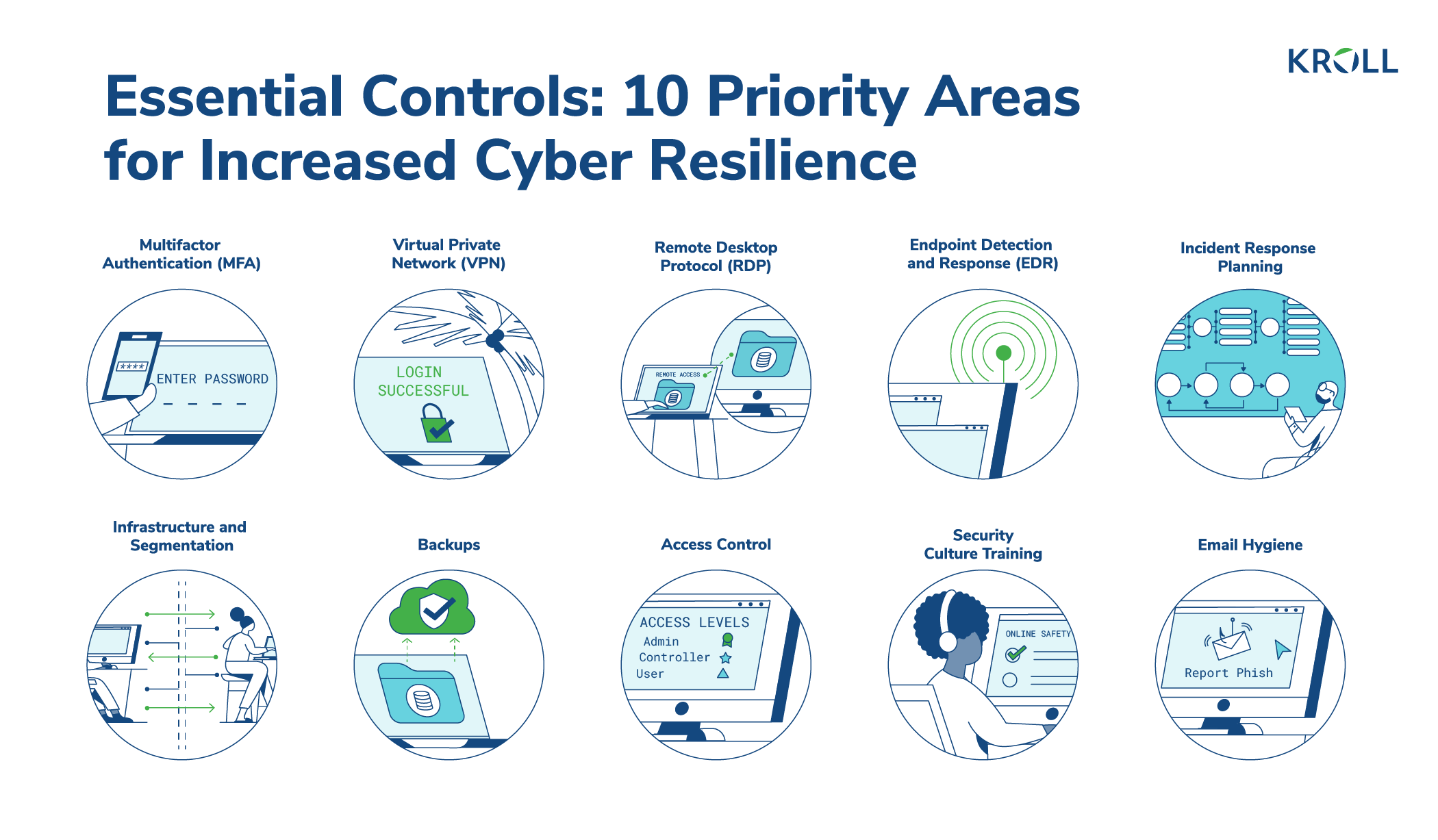
Implementing Multi-Factor Authentication Measures
As companies increasingly prioritize detailed protection procedures, one efficient approach is the application of multi-factor authentication procedures. Multi-factor verification (MFA) is a protection technique that calls for users to offer multiple forms of identification to access a system or application. This method includes an additional layer of defense by combining something the individual understands, such as a password, with something they have, like a security or a finger print token.
By carrying out MFA, organizations can substantially boost their safety posture - corporate security. Standard password-based verification has its limitations, as passwords can be easily compromised or neglected. MFA minimizes these threats by including an added authentication factor, making it harder for unauthorized people to get to delicate info
There are several kinds of multi-factor authentication techniques readily available, including biometric authentication, SMS-based confirmation codes, and hardware symbols. Organizations require to assess their specific needs and select the most ideal MFA option for their needs.
Nonetheless, the execution of MFA should be very carefully prepared and executed. It is vital to strike a balance between protection and usability to avoid customer disappointment and resistance. Organizations must likewise consider potential compatibility problems and provide adequate training and assistance to guarantee a smooth shift.
Enhancing Employee Awareness and Training
To strengthen business protection, organizations right here must focus on improving employee understanding and training. In today's rapidly progressing threat landscape, employees play a critical function in securing an organization's sensitive details and possessions. Several safety and security violations occur due to human mistake or lack of awareness. For that reason, companies need to buy thorough training programs to inform their workers about possible dangers and the very best practices for minimizing them.
Effective employee awareness and training programs need to cover a wide range of topics, consisting of data security, phishing attacks, social design, password health, and physical security procedures. These programs need to be tailored to the details needs and obligations of different employee roles within the organization. Routine training sessions, simulations, and workshops can aid employees establish the required abilities and understanding to react and recognize to protection dangers successfully.
Moreover, companies ought to encourage a culture of security recognition and offer recurring updates and suggestions to keep employees informed concerning the most recent threats and reduction strategies. This can be done with inner interaction networks, such as newsletters, intranet websites, and email campaigns. By cultivating a security-conscious workforce, organizations can significantly decrease the chance of safety and security occurrences and shield their important assets from unauthorized access or compromise.

Adapting Safety Actions for Remote Workforce
Adjusting business safety steps to suit a remote labor force is essential in making certain the protection of delicate info and properties (corporate security). With the enhancing fad of remote work, companies have to implement suitable safety actions to alleviate the risks connected with this new means of working
One critical aspect of adapting protection actions for remote work is establishing safe and secure interaction networks. Encrypted messaging systems and digital personal networks (VPNs) can assist secure sensitive info and protect against unapproved access. Additionally, companies must impose making use of solid passwords and multi-factor verification to boost the safety and security of remote access.
One more vital factor to consider is the execution of safe and secure remote accessibility options. This involves providing workers with secure accessibility to company sources and information through digital desktop framework (VDI), remote desktop methods (RDP), or cloud-based remedies. These modern technologies guarantee that delicate details continues to be protected while allowing workers to perform their duties successfully.

Lastly, extensive security recognition training is crucial for remote employees. Training sessions should cover best methods for safely accessing and dealing with sensitive info, determining and reporting phishing attempts, and keeping the overall cybersecurity hygiene.
Verdict
In conclusion, as the threat landscape proceeds to develop, it is vital from this source for companies to reinforce their safety and security measures both in the cyber and physical domain names. Incorporating cybersecurity and physical safety and security, executing multi-factor authentication steps, and boosting staff member awareness and training are crucial steps towards attaining durable corporate safety.
In this conversation, we will check out the transforming risk landscape, the demand to integrate cybersecurity and physical safety and security, the execution of multi-factor verification steps, the value of worker recognition and training, and the discover here adjustment of safety actions for remote workforces. Cybersecurity measures can be matched by physical safety procedures, such as security video cameras, alarms, and safe and secure access factors.
As organizations progressively prioritize detailed safety and security actions, one efficient method is the execution of multi-factor verification procedures.In verdict, as the risk landscape proceeds to advance, it is vital for companies to enhance their security gauges both in the cyber and physical domains. Integrating cybersecurity and physical protection, implementing multi-factor authentication steps, and improving staff member understanding and training are important actions in the direction of attaining robust business safety.